Security Engineering (SVE) Workbench
Return to the SE-Workbench Project Page Security Vulnerability Explorer ToolThe Security Vulnerability Explorer (SVE) is a software tool for Security Engineers involved in researching security vulnerabilities and weaknesses related to computer hardware and software. This tool can be helpful in understanding the various ways computer information systems are susceptible to attack, and th identify measures necessary to avoid or mitigate the risk of occurrence of defects and weaknesses that may be introduced in design, coding, integration or operation of computer information systems. The tool may be used as a learning aid, as a part of a Vulnerability Assessment, as a part of planning for security testing, or as a part of followup of discovery of a vulnerability, or an investigation of a security incident. To perform these Security Assessments Security Engineers will consult any of a number of authoritative reference documents concerned with Security Vulnerabilities and Weaknesses. The base documents for vulnerability assessments or vulnerability analysis include: Mitre Common Weakness Enumeration (CWE), Mitre Common Attack Patterns (CAPEC), the National Vulnerability Database (NVD), Mitre Common Vulnerability Enumeration (CVE), as well as other industry documents, such as Open Web Application Security Project (OWASP), and more The SVE tool provides a convenient way for the Security Engineer to explore the information in this grouping of reference information.
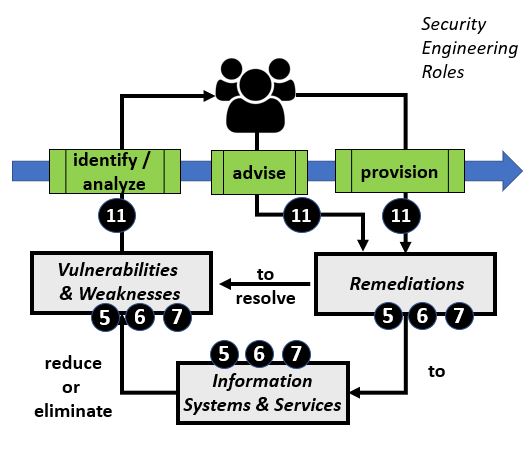
Security Vulnerability Analysis Process ReviewTable #1 below provides an overview of the Vulnerability analysis process and information resources. The left side of the table shows the basic process where security engineers perform a variety of tasks to identify, advise and provision remediations that map to relevant vulnerabilities and weaknesses on information systems and assets. The right side of the table calls out reference information used by security engineers.
Table #1 - Security Vulnerability Analysis
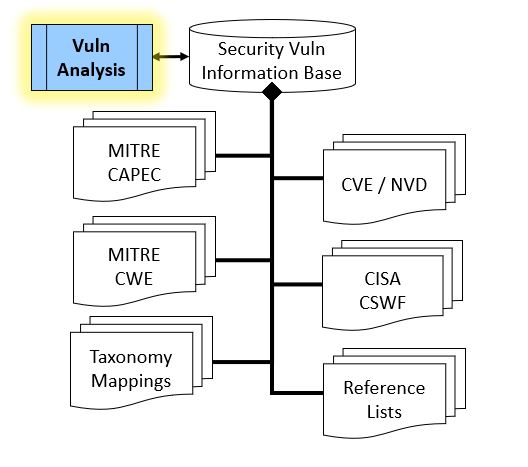
As shown on the right side of the Table #1 above, the primary document for the SVE tool is Mitre CWE. Each entry in Mitre CWE represents a potential weakness or defect. Each weakness or defect contains detailed information about the weakness, along with direct and indirect information to other (secondary) references in the document map. Each secondary reference contains detailed information, as well as references to other secondary documents or the primary document. SVE Tool OverviewTable #2 below provides an overview of the SVE Tool. The user interface for the tool is a web browser. The display can be divided into sections: the upper section is the header portion and the lower portion is the data portion.Table #2 - SVE Tool Layout
The upper section of the browser window, or Header, contains information about the tool, including release specific information, notes and acknowledgements. The lower section of the browser window, or Body, is the work area of the tool. The top of the Body contains pull down menus, search field and a set of column headers on for each of the major fields in the output. Middle portion of the Body is a data table providing a tabular view of the CWE entries. The content and ordering of the data table will vary depending which if any of the operators in the Header or Footer have been activated. The bottom portion of the Body displays the number of rows available to display in each browser page, the total number of CWE entries in the current display based on active filters in the Header, as well as a way to index each page in the current output set. Each portion of the display is described in more detail below. The primary document for the SVE tool is Mitre CWE. Each entry in Mitre CWE represents a weakness or vulnerability. Each weakness entry contains detailed information about the weakness, along with direct and indirect information to other (secondary) references in the document map. Eadh secondary reference contains detailed information, as well as references to other secondary documents or the primary document.
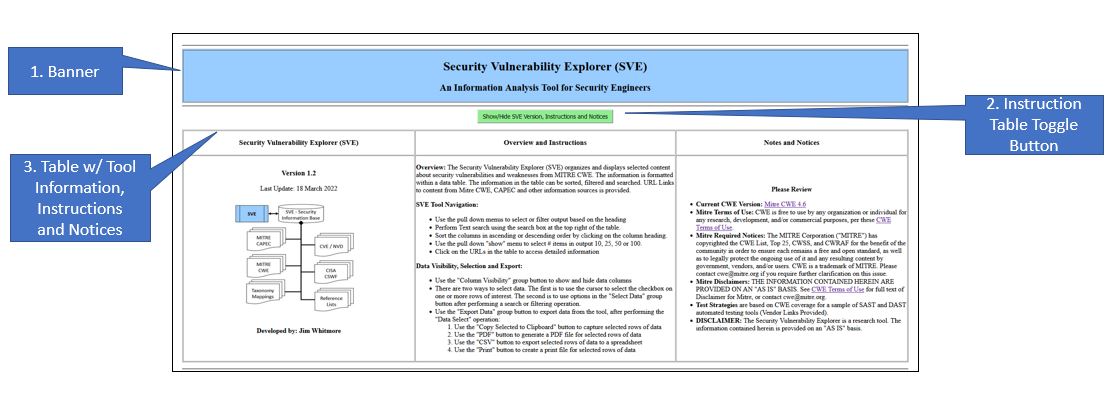
SVE Tool DetailSecurity Vulnerability Explorer Tool - Upper SectionThe upper section of the browser window, shown in Table #3 below, contains three areas of interest:
Table #3 - SVE Browser Window - Upper Section
The title of the tool is at the top. Information about the ownership, version and contact information is found in the left column. The left hand column also contains a basic document map associated with the tool. Basic usage instructions are located in the center column. Notes, Notices and Disclaimers about the tools, as well as terms and conditions from the owners of the information sources are located in the right column.
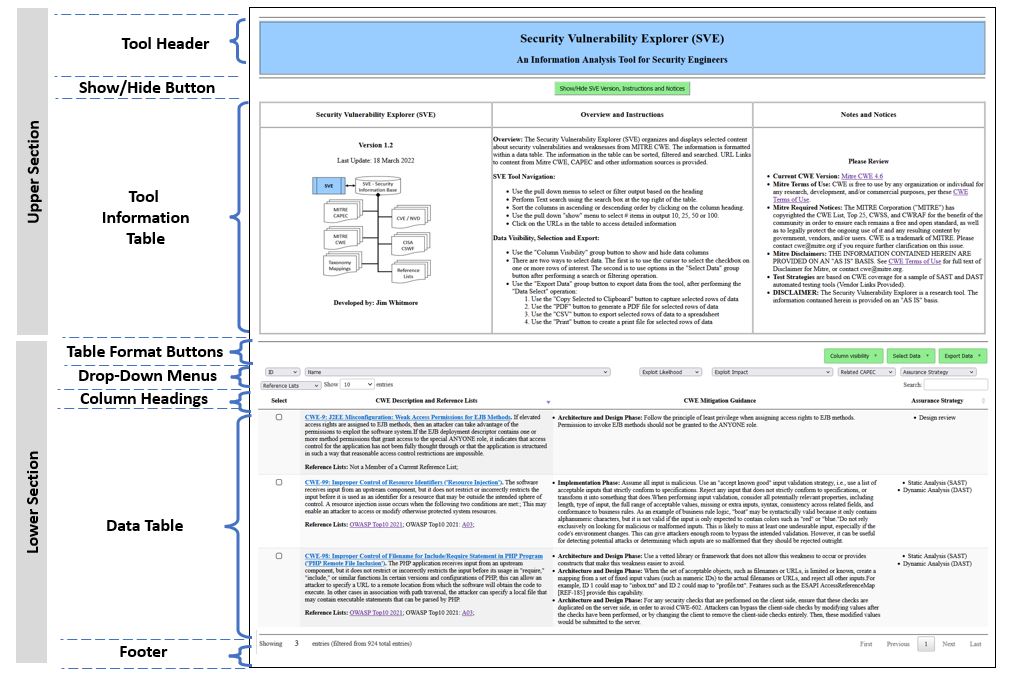
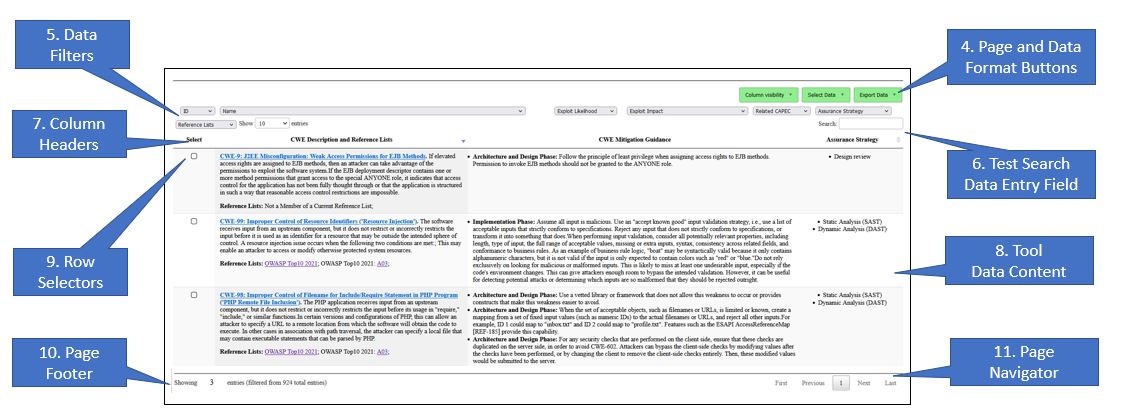
Security Vulnerability Explorer Tool - Lower SectionThe Data Table (identifed as item 8 in Table #4) is the focus of the tool. On initialization, the Data Table contains one row for each entry in the main reference document along with related direct and indirect references. For the Security Vulnerability Explorer, the main reference document is the version of Mitre Common Weakness Enumeration listed in the Tool Information Table. The data cells are constructed with information from the primary and secondary information sources, as well as derived data. The data cells may contain single data elements, grouped data elements or composite data. Derived data elements may include links to external referencces, data that is aggregated from one or more information sources, and/or knowledge insights. The size,content and order of the data table at any time is dependent on the user-driven operation. The Lower Section of the browser window, shown in Table #4, contains 8 areas of interest:
Table #4 - SVE Browser Window - Lower Section
The headings and buttons at the top of the Data Table are used to manipulate the information in the Data Table.
SVE Tool User OperationsThe SVE tool is designed to support the security engineer in evaluating and selecting security attack patterns that are relevant to a specific problem. to do that the tool provides the means for the security engineer to search, sort, select, review the available information on security attacks and export the findings for followup. When the tool is invoked, the Data Area contains the default view or the entire security information base. The user may perform operations in any order:
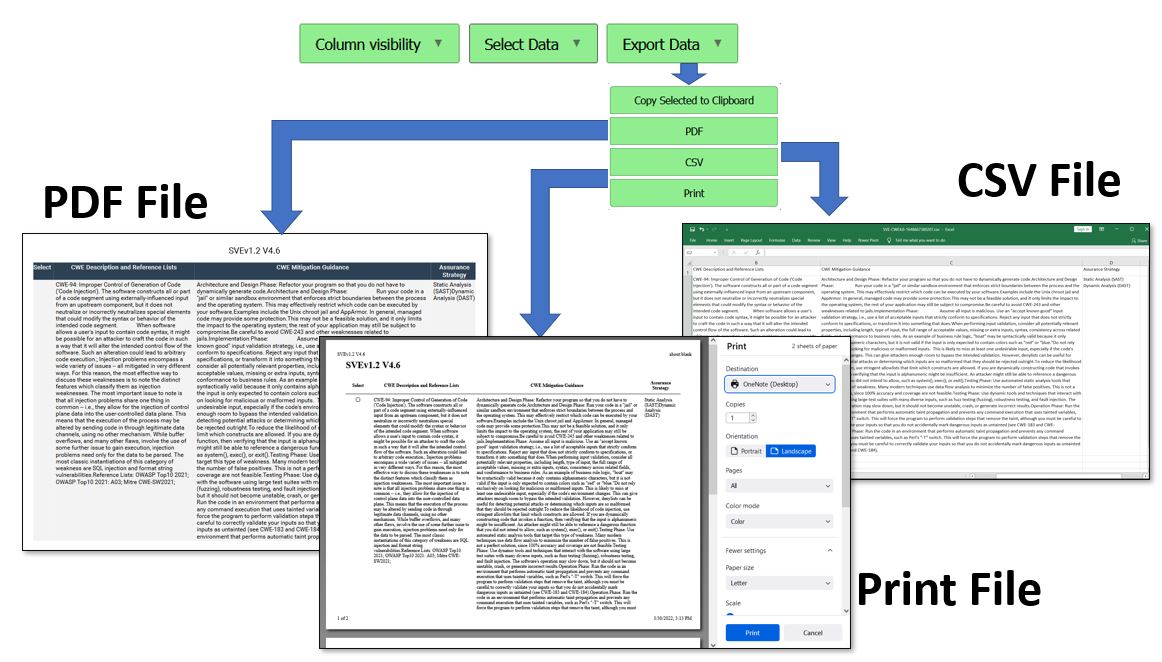
SVE Export Data Function
The Export function is used to create and store a copy of some or all the data in the tool in PDF, CSV or Print formats. The export function operates on data that has been selected. There are two ways to select data: (1) clicking on the checkbox of one or more rows of data, or (2) use the filter or text search features of the tool to narrow the focus of the visible data and then use the Select Data function to either Select All Data or Select Filtered Data. Table #5 below provides a visualization of the use of the Export function, where the user can select to "Copy Selected to Clipboard", generate a "PDF" diocument, generate a spreadsheet file in the "CSV" (Comma Separated Value) format, or create a "Print" file for local or network printing. The "Copy to Clipboard" function requires the operator to select a destimation application, such as Notepad, Word Processing Document or other. The PDF, CSV or Print options will automatically open a window to the corresponding application, assuming that the users computer system has a compatible application. Table #5 - SVE Export Data Function
Sample ExercisesRefer to the SVE Exercise link from the Project homepage for examples. |
Copyright © 2024 Jim Whitmore.
LAST UPDATE: 09 December 2024