Security Engineering (SE) WorkbenchReturn to the SE-Workbench Project Page Security Analysis Tool DesignThe goal of the SE-Workbench Project is to develop tools that aid in the gathering and analysis of information for Security Analysis. This page explains: the Security Analysis process, the Security Information Sources useful for various forms of security analyses, and the capabilities and underlying technologies on which the current tools are based.
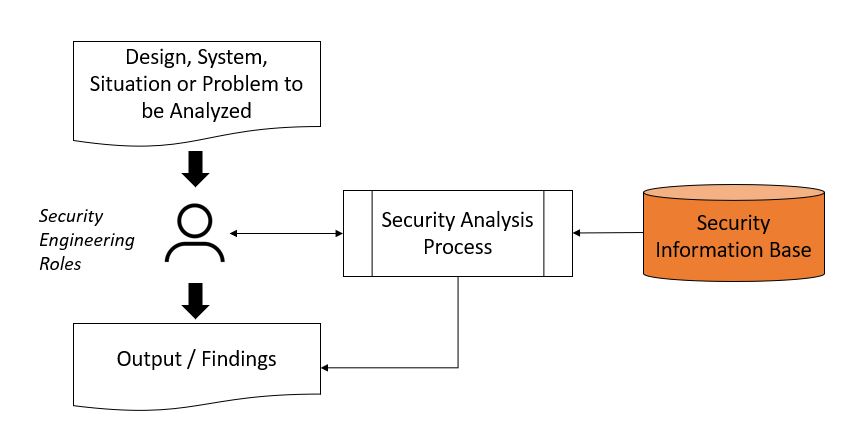
Basic Security Analysis ProcessThe basic Security Analysis Process shown in Table #1 below. The left side of the table illustrates to inputs and outputs of a Security Analysis, where the Security Engineer gathers information about the problem to be analysed, to include environment, business and technical parameters and variables, etc. Part of the analysis process includes processing reference information in relation to the problem at hand. The reference information is drawn from authoritative information sources. The right side of the table lists the basic steps that the Security Engineer follows in Security Analysis process, to include learning about the problem at hand, gathering information relevant to the system or problem being analyzed, performing the analysis or evaluation using critical thinking, situation analysis and deductive reasoning, and documenting results and opinions. The process inherently relies on iteration creating, testing and revising hypotheses along the way.
Table #1. Basic Security Analysis Process
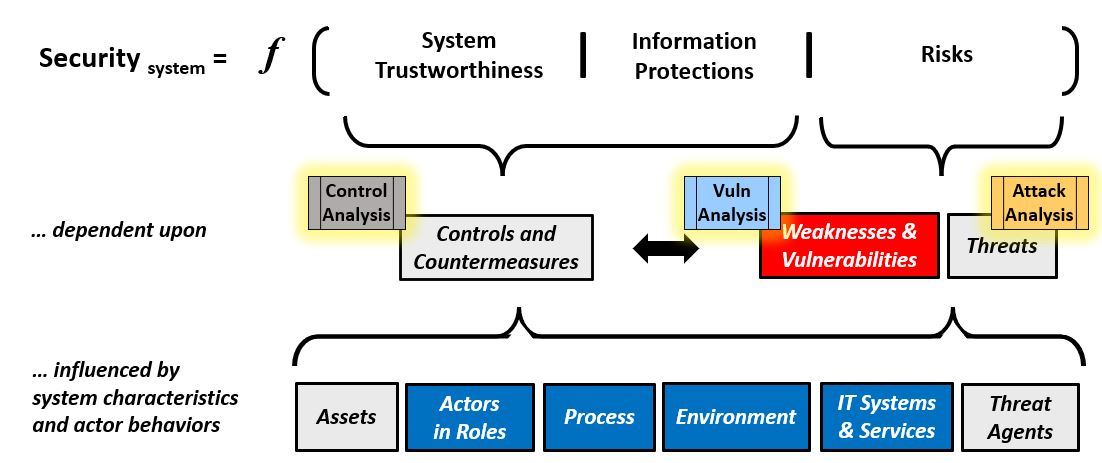
Applied Security Analysis ProcessThe basic Security Analysis process is adapted for use depending on the task at hand, and the reference information needed to perform the activity. There are three important variations of Security Analysis: Security Control Analysis, Security Vulnerability Analysis and Security Attack Analysis. Each activity requires a specific set of reference information.Table #2 below shows the relationship of three tools for Security Analysis: Security Control Analysis, Security Vulnerability Analysis and Security Attack Analysis to the diagram depicting Security as a Function.
Table #2. Security as a Function
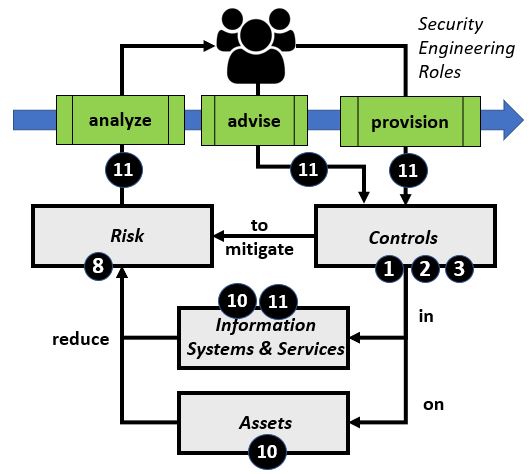
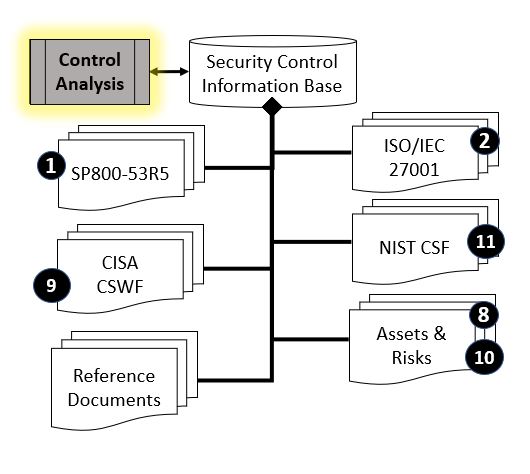
Security Control AnalysisSecurity Control Analysis, also referred to as Security Risk Analysis is a Security Engineering activity that is used to: (1) establish a baseline assertion of business and/or technical risk for an organization or computer information system, (2) establish a baseline set of security controls to address business and/or technical risk for an organization or computer information system, (3) assess current organizational and information technology controls and practices against a previously established baseline, or (4) document a plan for improvement of organizational and information technology controls and practices, in consideration of identified gaps, or as a result of security incident(s). In Table #3, the left side provides a general flow of work, where Security Engineers analyze or assess risk in Information Systems, Information Services and/or Assets per practices outlined in the Cybersecurity Workforce Framework or other reference. The Security Engineers advise on, and/or provision, updated security controls that will reduce risk in Information Systems and Assets. Security Engineers routinely refer to authoritative reference information for Security Controls, to include: NIST SP800-53R5, ISO/IEC 27001 and other sources.
Table #3. Security Control Analysis
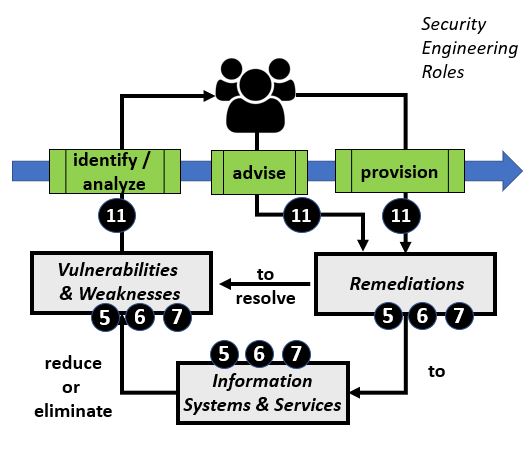
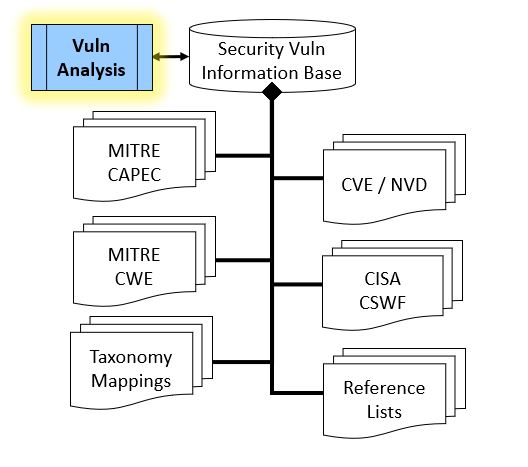
Security Vulnerability AnalysisSecurity Vulnerability Analysis is a Security Engineering activity that is used to: (1) examine and evaluate computer information systems for defects and weaknesses that may increase risk and/or enable Threats and Attacks, (2) develop a testing plan to identify and evaluate vulnerabilities in organizational practices or computer information system design, development, operation or maintenance, or (3) evaluate testing plans and practices to document a plan for improvement of for detection and remediation of vulnerabilities in accorgance with organizational policies security controls. In Table #4, the left side provides a general flow of work, where Security Engineers analyze or model threats and attacks to Information Systems, Information Services and/or Assets per practices outlined in the Cybersecurity Workforce Framework or other references. Security Engineers advise on, and/or provision, updated security controls that will mitigate threats and attacks on Information Systems and Assets. Security Engineers routinely refer to authoritative reference information for Mitre CWE, National Vulnerability Database (NVD), Mitre CAPEC and other sources.
Table #4. Security Vulnerability Analysis
Security Threat AnalysisThreat Analysis is a Security Engineering activity that considers the events and conditions that affect the reliability and correct operation of a system.Threat Analysis is used to: (1) establish a baseline assertion of about threats relevant to a business, organization or computer information system, (2) establish an action plan to mitigate threats to an organization or computer information system, (3) assess current organizational and information technology practices to mitigate threats against a previously established baseline, or (4) document a plan for improvement of organizational and information technology controls and practices, in consideration of identified gaps, or as a result of security incident(s). Threat Analysis is fundamentally different from Control Analysis and Vulnerability Analysis. The process and recommendations for Security Control Analysis and Security Vulnerability Analysis are prescriptive, that is, both have finite sets of options and alternatives to consider. Threat Analysis, on the other hand, requires consideration of combinations and permutations of a wide range of events and conditions that need to be evaluated and prioritized based on severity and likelihood that meets the risk management objectives of a given organization or owners of a specific computer system. Terms associated with Threat Analysis include:
Note: Comprehensive Threat Analysis is beyond the scope of the SE-Workbench Project, because of the limits of the Security Information Base used in the project.
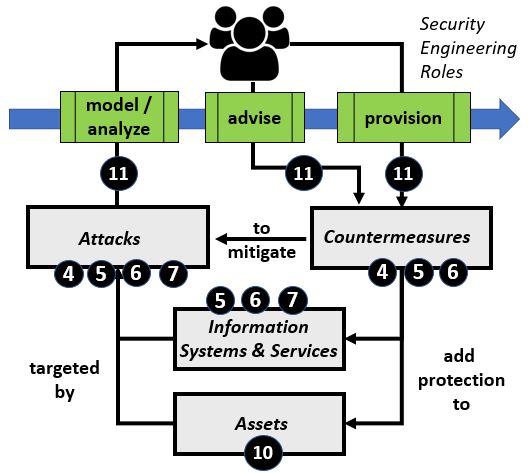
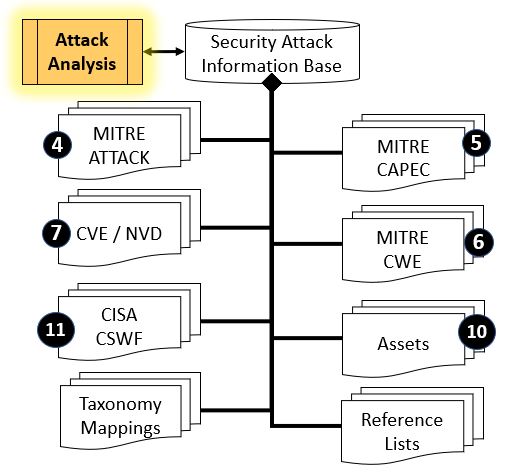
Security Attack AnalysisAttack Analysis is a type of Threat Analysis that focuses on an act against a computer system. Attack Analysis is supported by the security reference information described previously.In Table #5, the left side provides a general flow of work, where Security Engineers analyze or model threats and attacks to Information Systems, Information Services and/or Assets per practices outlined in the Cybersecurity Workforce Framework or other references. Security Engineers advise on, and/or provision, updated security controls that will mitigate threats and attacks on Information Systems and Assets. Security Engineers routinely refer to authoritative reference information for Mitre Attack, Mitre CAPEC, Mitre CWE, and other sources.
Table #5. Security Attack Analysis
Composition of Security AttacksTable #6 offers a way to think of and analyze security attacks, where a security attack is a single act that can be described as an array of information elements. A group of one or more security attacks can be organized into an "attack scenario". The entirety of attack scenarios that are relevant to a computer system represents an "attack surface". Table #6. Composition of Security Attacks
SE-Workbench ToolsThe SE-Workbench tools server two purposes: (1) to enable students and professionals to build skills and better understand the topic of cyber and information security, and (2) to provide easy and consistent access to information needed by security engineering roles who perform various forms of security analysis. The SE-Workbench tools are designed with a consistent look and intuitive operation. Each SE-Workbench tool operates on machine readable versions of security reference documents that relate to the focus of the tool. The function and capability of a given tool follows the Capability Model that was presented in the project introduction:
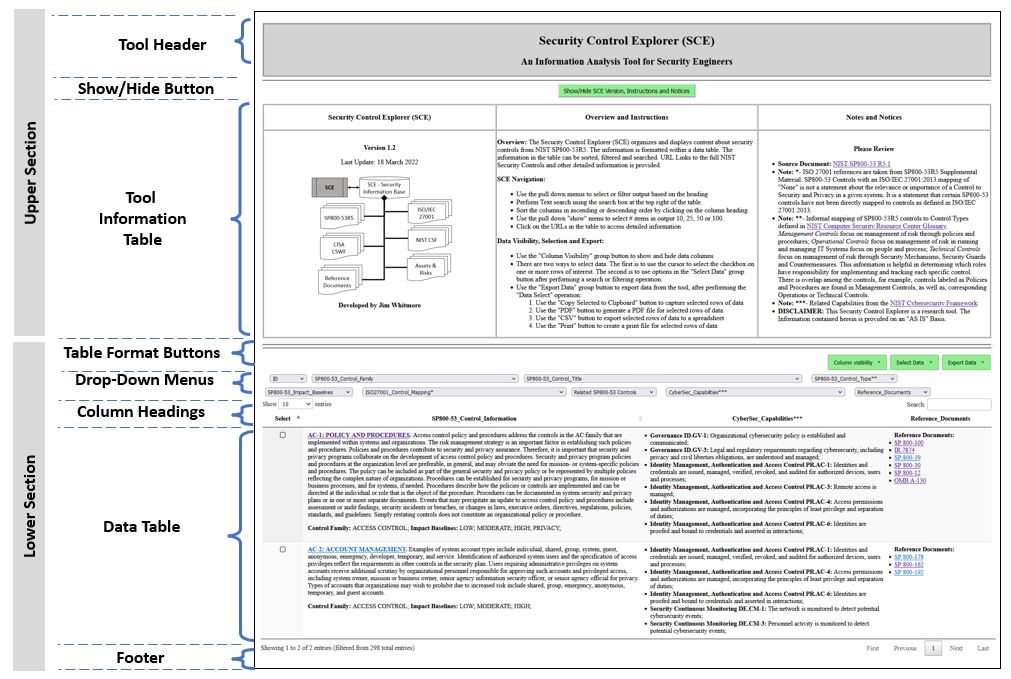
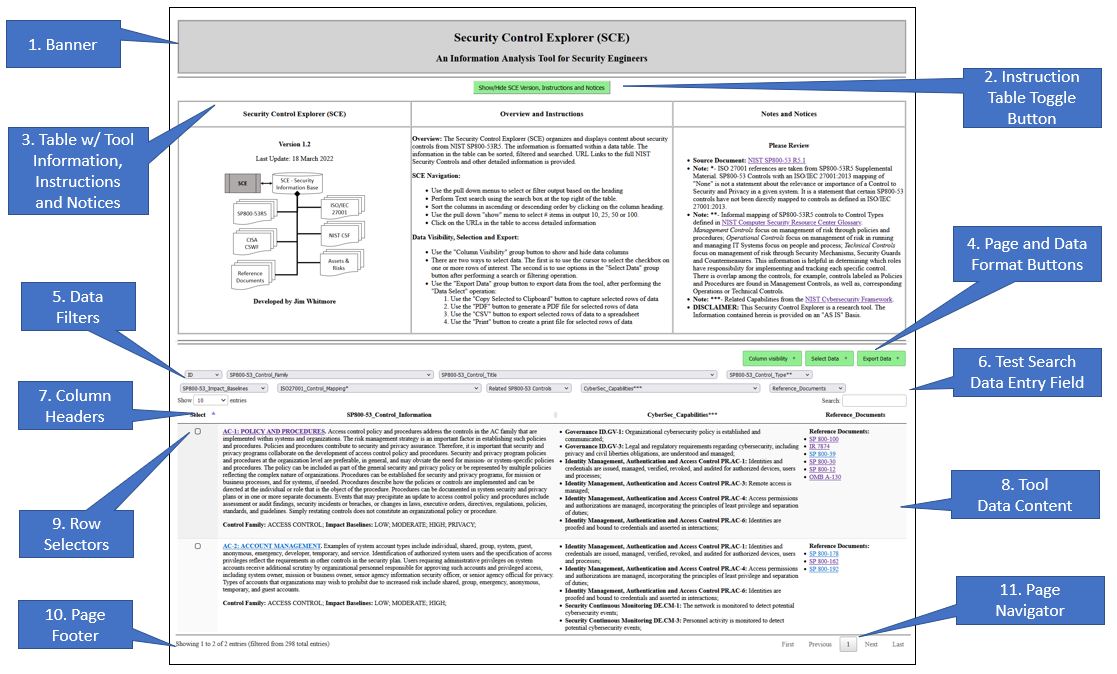
SE-Workbench ExplorersThe current SE-Workbench tools are "Explorers", providing visualization, data aggregation and data manipulation for a cluster of information sources relevant to the function of the tool. The tools also implement some capabilities of "Advisors", where the source data is augmented to resolve missing values, to identify affinity groups and create cross references.All of the "SE-Workbench Explorers" have a web-browser user interface. They are built on a common technology base to include: html, javascript, XML, XSLT, datatables and jquery. Tables #7 and #8 below show an example of a Security Explorer tool. This particular image is representative of the Security Control Explorer, or SCE Tool , that was introduced in Table #3 above. The user interface for the tool is a web browser. Table #7 shows the layout of the web browser page for the tool.
Table #7 - Explorer Tool Layout
Table #8 - Explorer Tool User Interface
The image in Table #8 above calls out eleven (11) areas of interest:
For More Information...The SE-Workbench project page provides links to each tool, along with a tutorial for the tool and a set of Sample Problems.
LAST UPDATE: 09 December 2024 |