Security Engineering (SE) WorkbenchReturn to the SE-Workbench Project Page An Analytial Model for Security EngineeringSecurity Engineers use critical thinking and deductive reasoning to analyze, identify, prevent and remediate anomalies and weaknesses in complex information systems. Common Criteria provides a General Model along with sets of Functional and Assurance Requirements for Security that form the basis for measurable trustworthy computing.
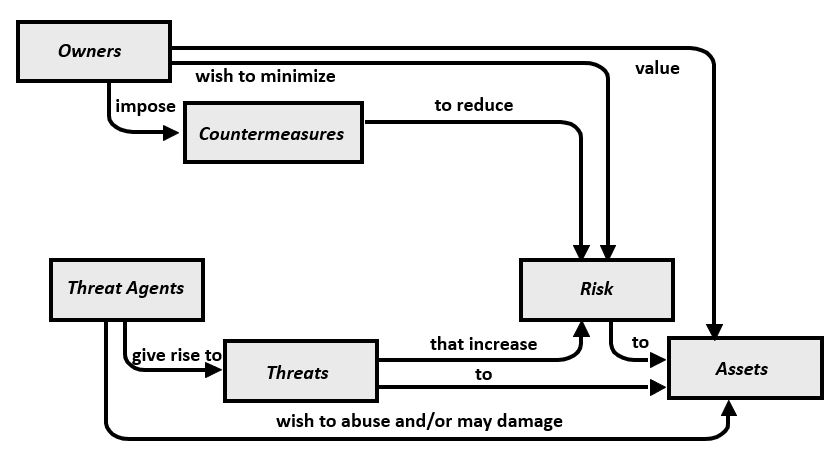
Security Model from Common Criteria (ISO/IEC 15408:2009)Common Criteria for Information Security Evaluation, provides an Information Security Concept and Relationship Model that concisely represents the conflicting factors that Security Engineers need to consider when performing Security Analysis. Table #1 contains a reproduction of the graphic from Common Criteria Part 1: Introduction and General Model. It illustrates a set of core security concepts and relationships. The graphic on the left side of the table is a visual representation of the relationships. The list on the left side of the table enumerates the assertions represented in the graphic.
Table #1 - General Model for Security
This figure illustrates the connection between Owners, Assets and Risks. It also calls out the interplay between Risk and Countermeasures. Common Criteria Introduction and General Model defines countermeasures as: "countermeasures are imposed to reduce the risks to assets. These countermeasures may consist of IT countermeasures (such as firewalls and smart cards) and non-IT countermeasures (such as policies and procedures). See also ISO/IEC 27001 and ISO/IEC 27002 for a more general discussion on security countermeasures (controls)."
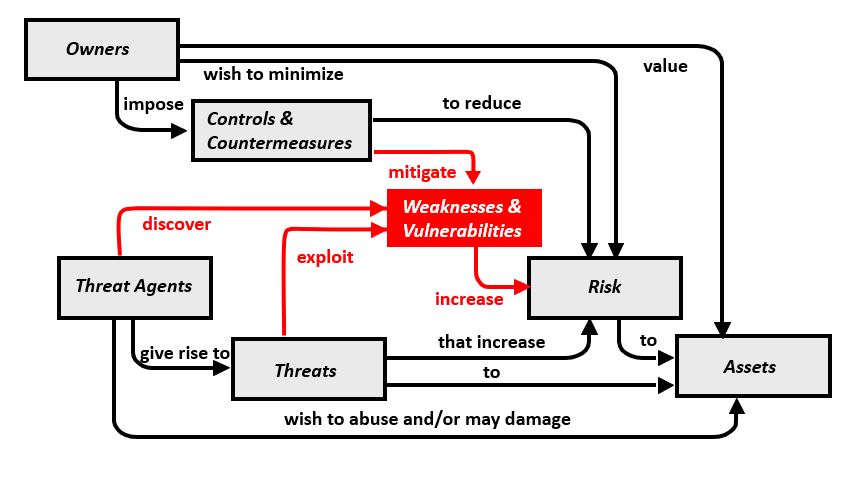
Security Model for Imperfect SystemsTable #2 expands the scope of connections between Owners, Assets and Risks by identifying the interplay between Security Controls, Threats and Vulnerabilities. This representation of the model differentiates between security controls that typically include policies and procedures as described by documents such as NIST SP800-53 or ISO/IEC 27001, and countermeasures that typically include security guards and technical mechanisms that are prescribed as a defense against a specific type of attack. This change provides the Security Engineer with the ability to investigate and plan for both types of risk response:
The diagram in the upper portion of the table provides a visual representation of the relationships. This list in the lower portion of the table enumerates the paths represented in the diagram.
Table #2 - Security Model for Imperfect Systems
This figure acknowledges that all systems may have flaws and weaknesses, and that these flaws and weaknesses provide opportunities for bad actors abuse and/or damage assets.
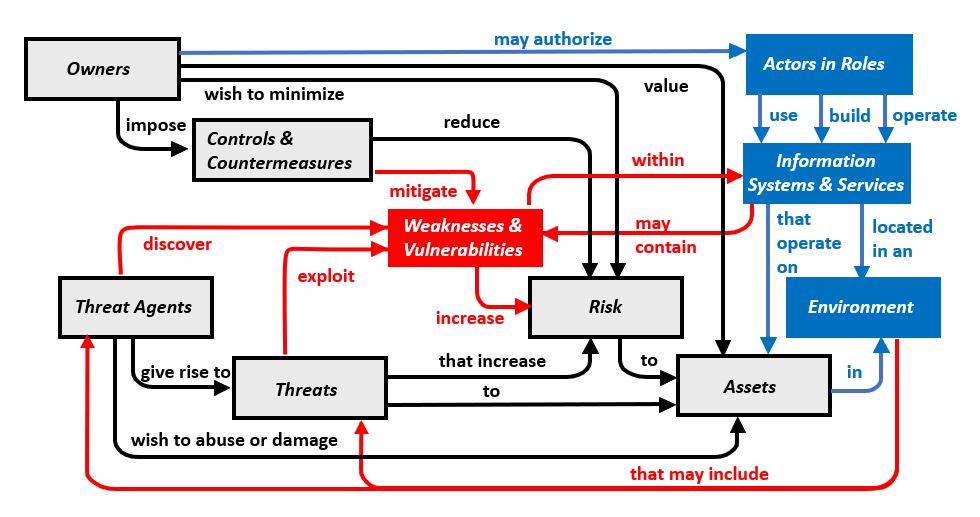
Security Model for Imperfect Information Technology SystemsTable #3 further extends the Base CC Model by illustrating the elements and relationships related to the building, operating and usage of Information Technology Systems that operate on Assets. This model recognizes the need for authorization of users in roles, and that Information Systems exist in operational environments that may contain threats and threat agents. The diagram in the upper portion of the table provides a visual representation of the relationships. This list in the lower portion of the table enumerates the paths represented in the diagram. The Model in Table #3 exposes the true complexity of the Security Engineering problem space.
Table #3 - Security Model for Imperfect Information Technology Systems
Security Engineers can use this set of Security Assertions to build the logic needed to perform Security Analysis.
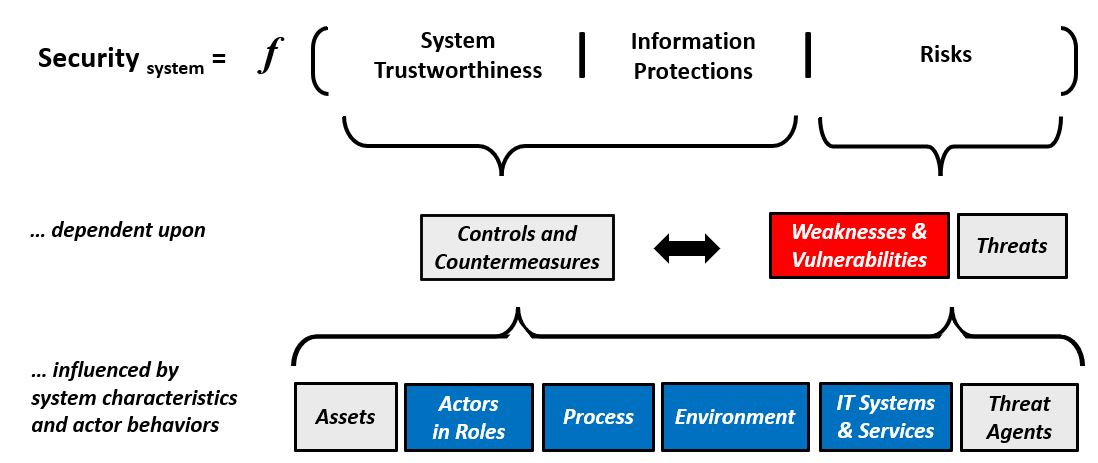
Security Analysis LogicTable #4 provides a view of Relationships and Dependencies that are relevant to Security Analysis. The formula expresses Security of a System as a function of Trustworthiness, Protections and Risks. These elements are dependent upon sets of controls, countermeasures, weaknesses and vulnerabilities. The elements are influenced by the characteristics and behaviors of the people, process, technology and information associated with the system.
Table #4. Security as a Function
Much of security analysis deals with the trying to understand and anticipate the behaviors of attackers who seek to bypass or circumvent security controls and countermeasures; or exploit vulnerabilities and weaknesses in the systems. This gives rise to the concept of "adversarial thinking" that juxtapositions the intent of system owners with the interest of threat actors and threat agents.
Adversarial ThinkingSecurity Analysis needs to position the motivation of the owner of assets against the motivation of attackers. This is referred to as Adversarial Thinking. Adversarial Thinking is routinely incorporated into Security Engineering tasks and activities, where some Security Engineers may act as members of Red Teams, i.e., attackers or ethical hackers, and some Security Engineers may act as members of Blue Teams, i.e., designers and defenders.Table #5 below, shows how the content from the bottom portion of Table #3 can be organized in a way that demonstrates the foundations of adversarial thinking for imperfect Information Technology Systems.
Table #5 - Adversarial Points of View
Table #5 illustrates the conflicting motivations and points of-view that contribute to the complexity of Security Engineering. On one hand, defenders work on behalf of owners and stakeholders of enterprises that include Information Technology Systems. On the other hand attackers see value in abusing or damaging assets belonging to the owner and stakeholders. Defenders and attackers act as adversaries in support of, or opposition to, the interests of owners. Attackers can be external threat actors or internal threat actors. Defenders can be any person or entity who is subject to the security policies of the owner(s). The role and task of being a defender is much more complicated than the role and task of being an attacker. Defenders need to get everything right all the time, and Attackers only need to be right once. Information Technology (IT) Professionals, to include Software Developers, Software Engineers, Systems Engineers and Security Engineers have a special role in ensuring that Information Technology systems are designed, implemented, operated and maintained with security and privacy in mind. IT professionals in the role of Security Engineers need to pratice Adversarial Thinking as the perform Security Analysis and apply their knowledge and expertise.
Copyright © 2024 Jim Whitmore. LAST UPDATE: 08 December 2024 |
 .
.